Parental Control Software
Children and computers are a double-edged sword. On one hand, computers offer learning tools delivered at such a rapid rate our children’s minds can fire on all cylinders. This offers the potential for higher intellect learning and, hopefully, a more successful future. On the other hand, aside from the social challenges computers possess, there is also the matter of safety. Type any private body part into Google images and see what your child is capable of viewing at any given moment. Ask your child how many ‘followers’ they have on their social media apps and you may get numbers way beyond the amount of friends you have ever comprehended having. Although we can’t wrap them in the safety bubble we’d like, what to look for in parental control software might alleviate some of your digital fears.
A Word on Privacy
Privacy is a tricky thing when it comes to your child’s safety. You’d like to offer them as much as possible. Explaining as early as you can the importance of computer limitations could help get them get used to the realities of online dangers. Let them know that parental controls will be turned on as full disclosure can often reap future trust on many levels down the line. Also, make it a rule to report to you any stranger attempting to communicate with them no matter how innocent it may seem. Online pedophilia is a serious and dangerous threat that can slip into any child’s digital life. With teens it can be a bit more tricky but if a discussion is offered at the right time you may be able to talk some sense into them. Spying is the last thing you want to do as many spy apps offers this, however if a child is struggling through specific challenges that warrant a parental override it may need to be done. Don’t rule out speaking to other parents and possibly a family therapist if this is the case.
Some Sobering Stats
To put things into perspective, a survey by Cox Communications and National Center for Missing & Exploited Children revealed that about only one in five parents use parental control software. Here are some findings from the survey:
- 44% admitted they’ve looked at or watched something online that their parents wouldn’t approve of (Only 28 percent of parents were aware of this).
- 34% have lied to parents about what they’ve done online. (Only 18 percent of parents were aware of this)
- 42% have received a personal message from someone they didn’t know. (Only 22 percent of parents were aware of this.)
- 17% have received an email or online message with pictures or words that made them feel uncomfortable. (Only 7 percent of parents were aware of this.)
- 12% have already been bullied by someone online. (Only 6 percent of parents were aware of this.)
Start Off Right
Finding the right parental control software for your needs requires some searching. It all depends on your comfort level, price range and technical aptitude (although most are pretty simple). It is often best to install this software before handing over a new computer to your child. You can be upfront and let them know that this software is there and that they can be tracked at any time. If it’s questioned then you can maybe let them know that when they are a certain age it will no longer be needed, kind of like a driver’s learning permit. Again, this is a fine line to walk for each family so the best and healthiest decision should be responsibly made as you see best.
In your search for the right software fit, you may run into various words that could sound menacing. Not to worry, it’s just the vernacular of the security industry. Here’s a few of the popular ones and what they mean:
Data filtration – This is usually an alert system that can be setup to respond to any specific words that trigger it. For instance, if your child types in the word “naked” your cell phone could receive a message.
Cloaking – Covert security alerts that are hidden in locations on your computer. This allows you to discreetly check activity and not have prying eyes (some kids do look) attempting to find and disable your software.
Invisibility – Similar to cloaking, there are adjustments you can make to some applications while others will tell you where alerts will be sent.
Keystroke duplication – This software will record every keystroke for your viewing.
Data access – This is how you receive alerts. Older versions require that you check the actual device you’re monitoring. The best data access is used remotely off your cell phone, tablet, laptop or desktop.
Texting Danger – There is even parental control software that includes alerts if your teen is driving and texting which is a major safety concern today.
Freebies
There is some free parental control software however it is important to make sure you are getting into something that doesn’t end up controlling you. Read the fine print.
Aside from the digital labyrinth of remote parental control apps there is always the old school (sort of) hands on blocking. This is basically activating password controlled parental options directly on your child’s phone, computer, game console, or television. These offer the ability to block specific website addresses or activate a standard option to disallow access to risky sites. It’s not foolproof though and sometimes additional software, such as those mentioned above, may be needed.
What to look for in parental control software means choosing the best fit for your specific needs. It is a great opportunity to introduce your child to the potential dangers of the digital world without making it a scary thing. Just like crossing at a red light, wearing a hat in winter or putting on a seatbelt, teaching your kid to be a smart, savvy online user will be yet another parental hurdle you’ve successfully achieved.
Glextor App Manager
Glextor App Manager is an alternative choice to your default app drawer to find and launch apps quicker. It’s key feature groups similar apps by category, i.e. Games, Productivity, Photo, Entertainment, etc. The grouping feature does not happen at first launch, however, you’ll have to tap the icon to the top left to allow the app to automatically filter. Thereafter when you add new apps they get automatically grouped. You can sort by all apps, downloaded apps and favorite apps and these too are sub-grouped. Additionally, you can create, edit and reorder groups; plus backup and restore group settings.
Furthermore, simply tap to open an app or can long-press to reveal more options like; creating shortcuts of apps and groups on the home screen, uninstall (individually or batch uninstall apps), share via Facebook, Gmail or text message, move to another group or view in Google Play. Diving into the settings reveals that you can change of theme (dark/light), navigation type, change icon size & language, grouping options and more.
I’m not a fan of ads in my app drawer, however, so if you try out the freebie version and find it useful you might want to consider the paid version to eliminate these.
I would encourage you to try the free version as it offers the convenience of grouping your apps to make things easier to find versus a long alphabetically organized list of apps offered by default Android and other custom skins many phones have. Though the app does not have a long list of features the few it does offer are worth checking out.
ESET Mobile Security
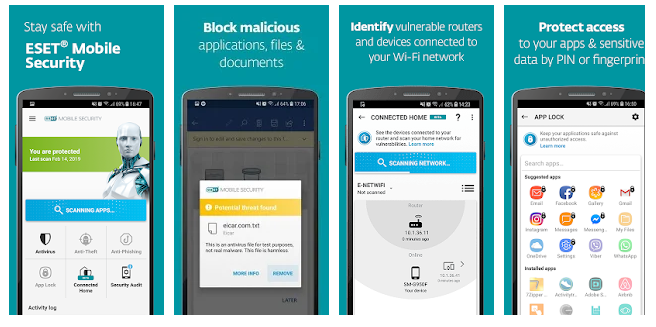
ESET Mobile Security is an antivirus, anti-theft and remote control app for Android devices. It comes with a powerful cloud-powered antivirus which scans each app or file you download for malware and enables you to customize its settings. For example, you can trigger a device scan each time you plug in your smartphone or tablet for a recharge or schedule it to run at a specific time of day.
If you ever had the misfortune to look for a missing device, you know that reuniting with it might be a tall order.
Imagine that you have returned from a walk just to find that you’ve lost your smartphone. Using my.eset.com, you can track the device’s location, get photos from its surroundings, and if you are around remotely trigger a loud siren, even if it is in silent mode. If your worst fears are confirmed and your device is gone irretrievably, you can still wipe its data clean remotely to make sure it stays private.
Should you lose your device, without being aware of it, Proactive Anti-Theft automatically takes preventive steps, which might help you retrieve it later.
If your device hits critical battery levels, its last location is automatically sent to your account on my.eset.com.
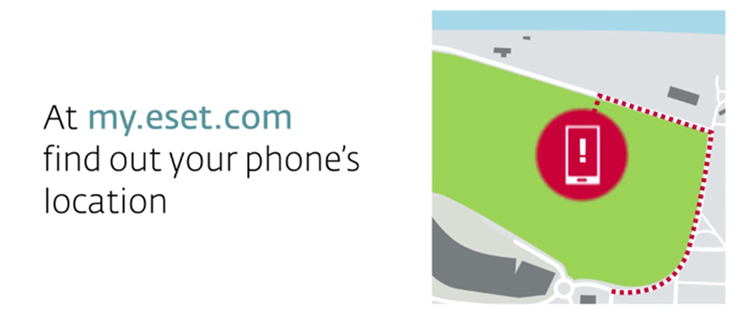
The Proactive Anti-Theft gets also activated if a wrong PIN/pattern is entered, or when an unauthorized SIM card is inserted.
If this happens, the feature automatically locks the device, starts tracking its location and sends camera photos of its surroundings to user’s account on my.eset.com web interface. It then sends you an e-mail notification to keep you up to speed.
This all-in-one security runs silently in the background and offers a variety of additional security tools on top of cloud-powered antivirus and Proactive Anti-Theft all designed to protect your device and privacy.
The ESET Mobile Security app is available on Google Play Store. Ditch your security worries − try the latest ESET Mobile Security, no commitment. A single license protects up to 5 devices connected to the same Google account.
Android Malware
If you’re walking in the mall and someone politely asks you to hand over your watch and other valuables and if you give it to them, have you just been robbed? I mean they did ask for your permission, and did so nicely! The same scenario has been taking place recently with malware on Android smartphones all over the world. Leading many to ask the question, “Is it still malware if it asks permission first?”
According to Google, the answer to these questions is yes. Recently, Google has established tougher guidelines for developers submitting apps to the Play Store in an attempt to cut down on malicious apps surfacing on its Android operating system platform. The new policy will include changes such as new rules on naming apps, more payment policy details and a ban on apps that disclose personal information without permission.
The cause of such changes may be linked to recent reports of malicious malware being hidden in fake Android apps found in the Play Store. Disguised as popular games such as “Super Mario Bros” and “GTA 3 Moscow City”, the malware wasn’t detected and removed until it was downloaded 50,000 to 100,000 times by unknowing consumers.
These apps are not the first to hide behind permissions accepted by consumers and are definitely not the last; even many legitimate apps request the same permissions. For quite some time, Android users have been complaining of excessive permissions. Apps that request excessive permissions to device information, access to personal information, and unusual levels of location information have been available for a long time, and are still available today.
But some say simply creating a new policy just isn’t enough, and Google has to find ways to block spyware apps from reaching the Play Store in the first place. Google has long been criticized for taking a ‘hands-off’ approach by not requiring app developers to go through an approval process when submitting apps, though they have made some small strides with the addition of their automated scanning service known as “Bouncer”.
With the implementation of Bouncer, Google has reported a decrease in malicious apps by almost 40 percent. Bouncer scans new and existing apps for known malware, spyware and Trojans. In addition, it also analyzes new developer accounts to make sure previously rejected developers and ones with a history of questionable apps stay out of the marketplace.
Today, many still criticize Google for choosing openness over user safety by not taking more proactive preventative methods in their Android app security. Recent tests have shown Bouncer’s flaws of not detecting and removing malicious content until after it has already entered the store and been made available for download.
It’s one thing to see malware on other online third party Android app stores, it is something completely different when they start sneaking their way into the official Google Play Store. The ‘openness’ of Google is great, but it may want to take just a few pages from iOS as far as permissions and app approval is concerned to make and keep the Play Store safe for its Android users.
RoboForm Password Manager
 It seems that every time you turn around you have to create another account, and remember yet another password. This problem is easily resolved by creating a few passwords you can remember with ease, and cycling them through your different accounts. For security purposes, you should never use the same password with any account for too long.
It seems that every time you turn around you have to create another account, and remember yet another password. This problem is easily resolved by creating a few passwords you can remember with ease, and cycling them through your different accounts. For security purposes, you should never use the same password with any account for too long.
The Problem
The problem with all of these different accounts and passwords is the requirements to set up the username and password. It becomes more difficult to use a handful of the same passwords and usernames when one site wants you to create a 25 word password that contains four words separated by a number and at least one symbol and a capital letter. In addition, there is a spy software that allows the user to collect your passwords without your knowledge.
The Solution
RoboForm is a password application that can resolve this problem for you. It is a new program that will give you unlimited access to all of your data. You can gain access from several different computers, smartphones, tablets, and any other mobile device. It is a flawless way to access multiple accounts and other types of data from the same place. The best part is you just need one license to do it all.
Features RoboForm Offers
This is a program for individuals who need to access accounts, bookmarks, safe notes, and data from multiple computers, laptops, and mobile devices at the same time. It is an easy way to keep a secure backup of all your important data. It is a convenient way to manage your data from anywhere.
Downloading and Installing
 You can download RoboForm for a Windows PC or a Mac computer. When the installation is running, make sure you check the “Everywhere” option. You will need to create an account with RoboForm and install it on all of your computers and mobile devices. Login to the same RoboForm account on all computers.
You can download RoboForm for a Windows PC or a Mac computer. When the installation is running, make sure you check the “Everywhere” option. You will need to create an account with RoboForm and install it on all of your computers and mobile devices. Login to the same RoboForm account on all computers.
Download RoboForm for free: https://www.roboform.com/download
You can install the application using iTunes, the Windows app store, or Google Play. After you install it, the program will work the same way on every device you have it on. Every time you make a change to your application or data, it will automatically update on all of your computers and devices.
Security
The biggest concern with using a program like this is the security. Is this program a safe place for you to keep all of your secure data, passwords, and login credentials? For the makers of this program, nothing is more important than the protection of your data and the privacy of your information.
All of your passwords are encrypted using a master password created by you. There are also strict guidelines in place that prevent anyone other than you from accessing your account. This means that no one but you will be able to get on your account without knowing what your master password is.
Conclusion
This is a program that is completely free the first ten times you login. If you have more than 10 logins, you will need to upgrade your account. You can pay a one time license fee of $29.95 to install this software. To install it on additional computers, you will have to purchase more than one license.